What comes to mind when you hear the word “security?” You might think of things like antivirus software, password authentication for smartphones, and security cards such as for buildings and residences. This time, we will introduce the security to be implemented in IoT devices.
I have been in charge of marketing for the security of the RX 32-bit MCU family for about 3 years. When I initially asked about security, there was just an image of antivirus software. I was wondering, “Microcontroller security features?” “Why would you need that?” “Who's going to attack?” However, the message I want to strongly convey to everyone now is, “Please immediately implement security measures on any IoT device!”
The growth in the market for IoT devices is increasing rapidly, and it is said that the CAGR (2018 - 2025) will continue to grow at a very high rate of about 30%, especially in the industrial sector. On the other hand, threats that attempt to exploit the network are also on the rise. Piggybacking on the coronavirus disaster, cyberattacks on network devices including IoT devices, are said to have increased by 260% from January to September 2020 compared to the same period in the previous year. Examples of cyberattacks include the following:
- Software vulnerabilities were exploited on nearly 100,000 IoT devices, with encryption keys stolen, devices being used as a springboard, and simultaneous DDoS attacks being launched on major DNS servers, making internet services unusable.
- In medical institutions, the IoT devices monitoring fetuses were hacked, slowing down the response of the devices.
This reference video shows examples of malfunctioning equipment that were used in attacks without the actual user's knowledge. These cases are frightening, aren't they? The damage caused by these attacks was not just from the actual attack, but also damage to the brand images of manufacturers selling IoT devices.
Due to these situations, there is a movement around the world to formulate IoT device security guidelines. In Japan, there is the Ministerial Ordinance on the Security of IoT Devices which has been in effect since April 2020, and in California, USA, an IoT Security Law has been in effect since January 2020. Security measures are becoming essential for IoT devices.
In light of this, what security measures are needed for IoT devices?
For instance, are you aware of the dangers of theft of or tampering with billing data, the theft of programs or the algorithm that is intellectual property, or that imitations could be made? The risk of a third-party attack cannot be zero as long as there is a network connection.
In order to mitigate these risks, security needs to be deployed, especially in the IoT devices that are the endpoints, and the RX security solutions make it easy to deploy strong security, contributing to the early development of safe and secure IoT devices. Please watch the on-demand seminar for more information.
The RX security solutions provide a unique hardware technology, Trusted Secure IP (TSIP), which stores key data and includes a monitoring circuit to protect against unauthorized access, resulting in very strong key management compared to a typical general-purpose microcontroller. Key data plays an important part in encryption and decryption. In a manner, it is like a PIN for a cash or debit card. Just like your PIN makes it secure, and you don't have to worry about stolen cards by themselves, RX security solutions are safe because even if your software has bugs or vulnerabilities, your most important key data is protected in the TSIP.
So, let's take a look at some of the RX security solutions.
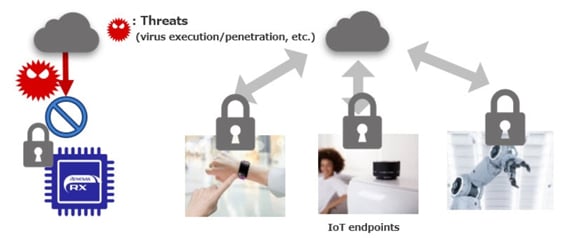
Figure 1. Strong Protection on IoT Endpoints with RX Security Solution
① TSIP exclusive driver: Many APIs are provided, and the encryption/decryption operation is performed easily.
② Renesas Secure Flash Programmer: A tool for encrypting keys and programs
③ Secure Boot Program
④ Secure Firmware Update Program
⑤ Development Kit
For more details and usages, etc., please refer to the RX Security Solutions page.
RX Security Solution: Usage Case - Smart Meters
Smart meters require security features in order to protect billing information and personal information. In conventional general-purpose microcontrollers, important key data has been stored in an internal ROM, so there was a risk of theft of key data theft as well as information leakage. RX's strong TSIP key management ensures secure key access and regular key updates that meet the customer's security requirements.
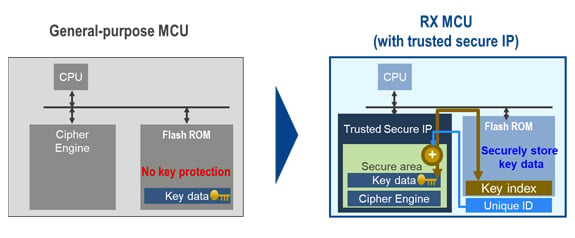
Figure 2. Features of RX MCU with Trusted Secure IP
- Electronic Locking Systems
Here we introduce an example developed using the “Communication Security Evaluation Kit,” which is one of the RX security solutions for electronic locking systems. Although electronic locks require firmware updates to ensure security and had high development hurdles for customers, our secure firmware update program was a great way to contribute to early development, and our customers were also very pleased.
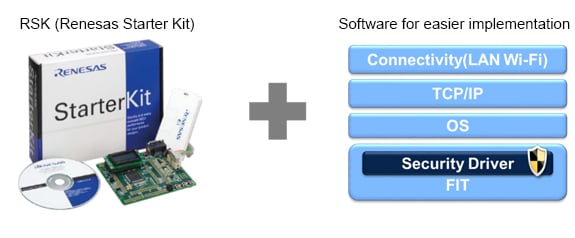
Figure 3. Development Kit and Software
As mentioned at the beginning, the need for security is increasing. On the other hand, there are barriers to the introduction of security such as the following:
- How to introduce security?
- There are insufficient resources to implement the security.
RX security solutions include dedicated drivers, applications, sample programs, and evaluation kits to address these challenges, and for your consideration to deploy security now.
For more details on the RX MCU, visit our RX 32-Bit Performance / Efficiency MCUs page.



