Get to know this life changing technology: 3 of 5
USB Type-C® Receptacle
To further improve convenience, USB Type-C has a vertically symmetrical design that allows it to be used commonly by both host and device sides. For this reason, as shown in Figure 1, the USB Type-C connector consists of two sets of 12-pin signals to enable upside-down insertion (interchangeable). The USB Type-C receptacle has a signal line (CC: Configuration Channel) dedicated to communication related to USB-PD, and an SBU signal that is a low-speed signal channel dedicated to alternate mode and USB4 in addition to the legacy USB signals. Note that when the receptacle is assembled on the back side of the board, the order of the signals will be reversed, but this cannot be seen visually.

Figure 1: Pin assignment for USB Type-C receptacle
USB Type-C Cable
As shown in Figure 2, a standard USB Type-C cable has USB Type-C plugs on both ends of the cable, and either plug can be inserted into the receptacle of either the Source or Sink device (left and right reversed insertion). Cable types in USB Type-C are defined as conventional passive cables, active cables that solve signal attenuation, optical cables that communicate data using optical, and hybrid cables. As shown in Figure 3, a semiconductor identification component called an e-Marker can be mounted inside USB Type-C plug in order to indicate the capability of the cable. The system can identify the cable type by communicating with this semiconductor component.

Figure 2: Pin assignment for USB Type-C cable

USB Type-C cable with e-Marker
Ra ranges 800-1200 ohm
Standard USB Type-C cable
Figure 3: Equivalent circuit for USB Type-C cable
Figure 4 summarizes the cases that occur when device A on the left side and device B on the right side are physically connected by using a standard USB Type-C cable. There are four cases in which each device's CC is physically wired via a standard USB Type-C cable. So, to understand how device A and device B are connected to each other, a connection sequence that differs from legacy USB methods is required.
The connection sequence for USB Type-C
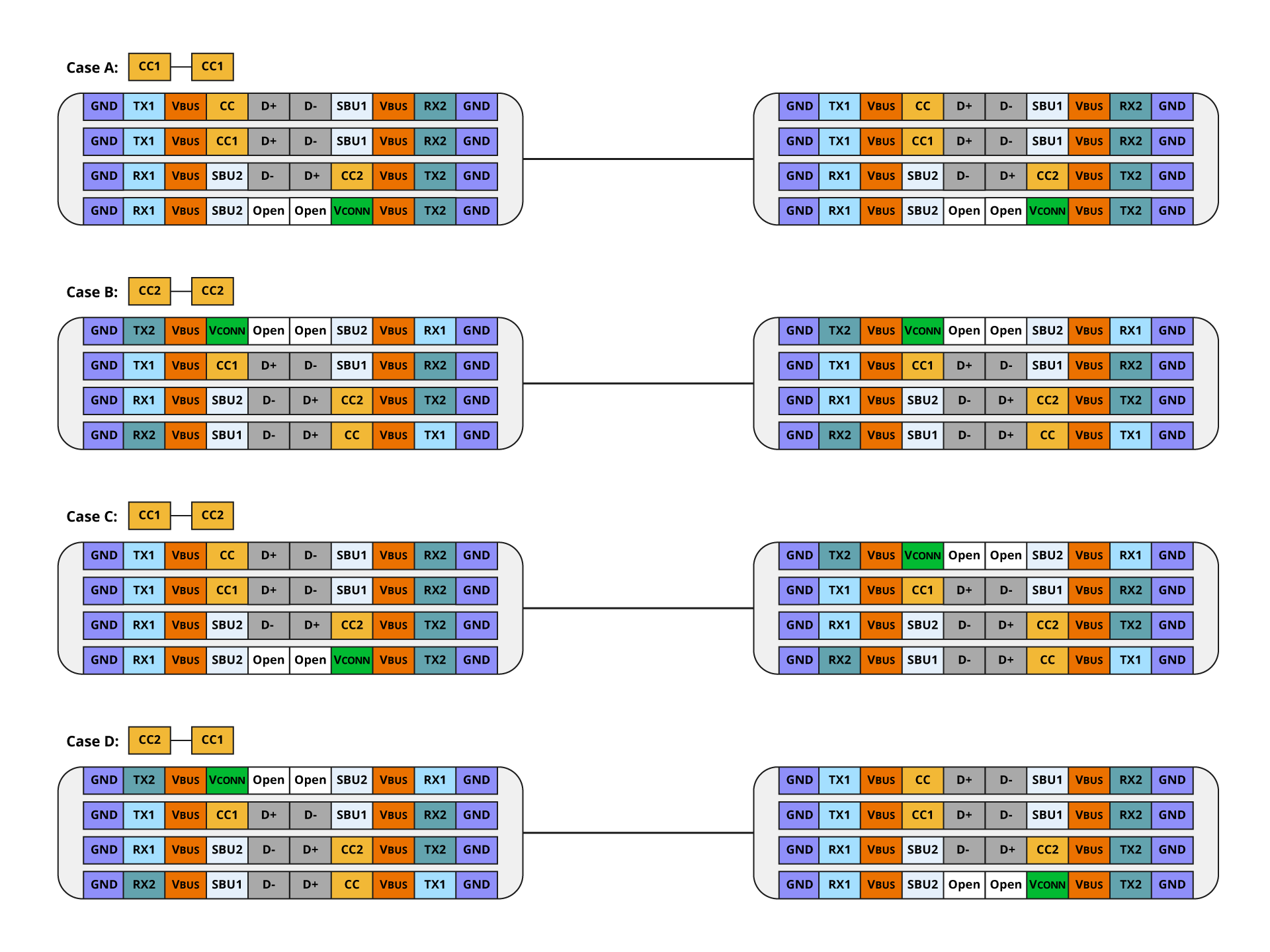
Figure 4: Physical connection by using USB Type-C cable
Legacy USB-A plugs could only be connected to host ports or USB AC adapter ports (called DFPs), and USB-B plugs could only be connected to device ports (called UFPs), host and device roles were automatically determined upon connection. On the other hand, USB Type-C is not only four physical connections mentioned above, but it is also physically possible to connect PC to PC, peripheral to peripheral, and AC adapter to AC adapter. Therefore, An additional process is required to determine the role for each port.
This is achieved by observing the potential level on the CC1 and CC2 lines. The Source is specified to pull up CC and the Sink is specified to pull down CC as shown in Figure 5. As shown in Figure 6, when a Source and a Sink are connected by using a USB Type-C cable, the potential level on CC becomes the voltage (vRd) range that should be identified as a connection. By monitoring the CC voltage level of both the Source and Sink, you can detect the connection and determine how the USB Type-C cable is connected to the receptacle.
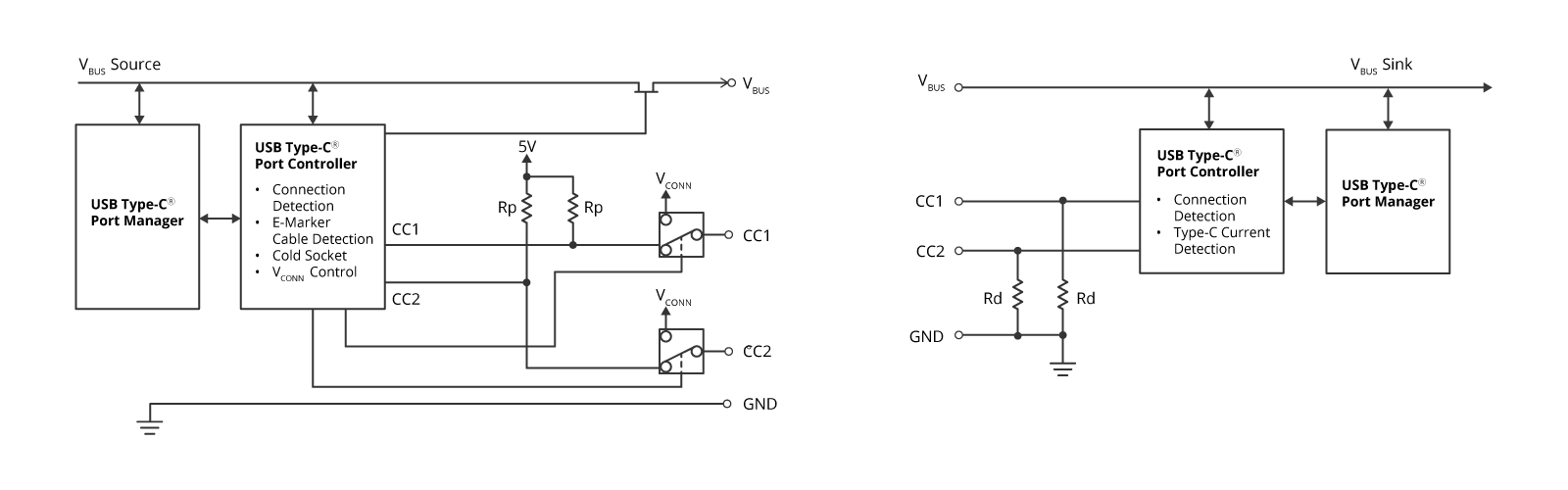
USB Type-C Source
The source requires CC1 and CC2 to be pulled up at 56k, 22k, or 10k. This resistor value indicates the power supply capacity on Type-C (Default, [email protected], 5V@3A)
USB Type-C Sink
The sink requires CC1 and CC2 to be pulled down at 5.1k.
Figure 5: Equivalent circuit for Source and Sink based on USB Type-C
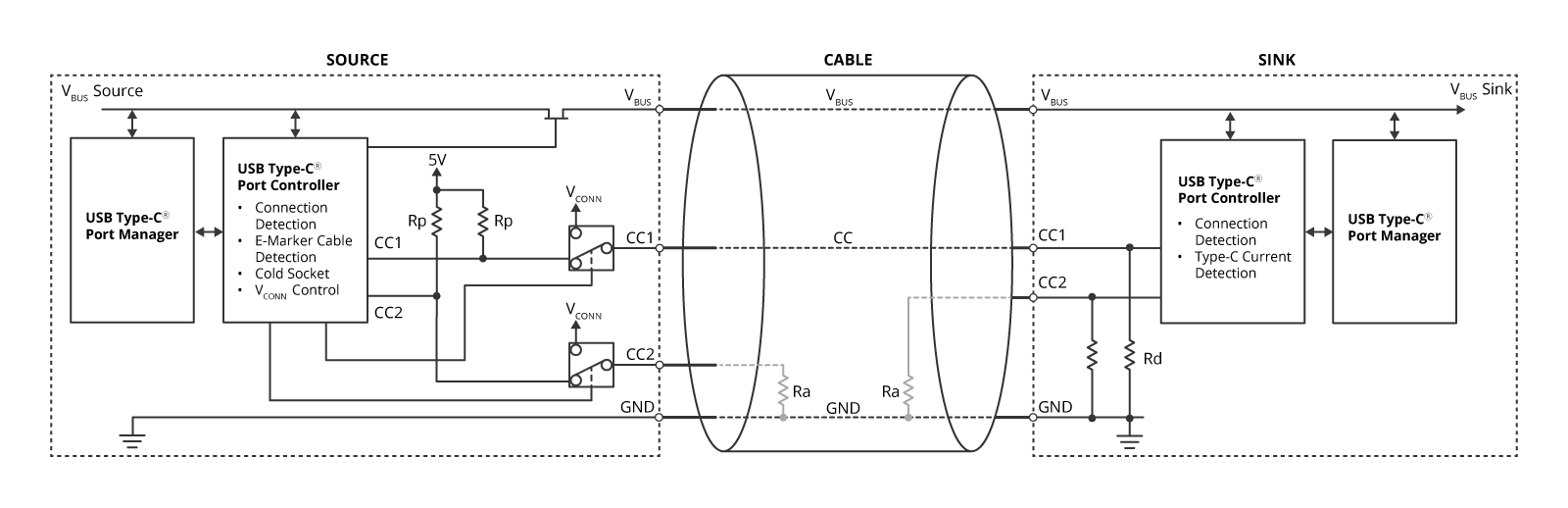
Figure 6: Attachment detection
Ra will be open if there is no e-Marker on USB Type-C cable. If it is confirmed that Ra exists, it can be recognized that VCONN, a dedicated power supply, is required to communicate with the e-Marker. At that time, Sources that support more than 3A current or EPR, or DFPs that support USB4 or alternate mode, must remove Rp from the CC pin and supply VCONN power.
On the other hand, if two sources are connected to each other as shown in Figure 7, the voltage level of the CC pin will be outside the voltage range that should be recognized as a connection. In this state, it is not good from a safety perspective that both sources supply power to VBUS, so VBUS is required to remain at 0V until a connection is detected. This state is called “Cold Socket”.

Figure 7: Connection between two sources
As well as, even if two sinks are connected to each other as shown in Figure 8, the voltage level of the CC pin will be outside the voltage range that should be recognized as a connection, too.

Figure 8: Connection between two sinks
Next, we will summarize the additional connection process for USB Type-C.
- Source-to-Sink attach/detach detection
- Plug orientation/Cable twist detection
- Initial power supply direction (Source-to-Sink) detection and the establishment for the data communication (Host-to-Device)
So far, VBUS = 0V : Cold socket and VCONN = 0V. - Detection if cable requires VCONN and supplies VCONN
Although VBUS may supply 5V, but never consume the power on sink. The VCONN source must supply 3-5V (5V is for ThunderBolt3 Active cable compatibility) to cable if cable does require VCONN. - USB Type-C VBUS current detection
The sink detects as connected when CC voltage = vRd (identification voltage range) and VBUS = 5V. The power supply capacity on USB Type-C that does not support USB PD is defined as "Default", [email protected], and [email protected], and the sink identifies the power that the source can supply from the monitored CC voltage level. Therefore, up to this amount of power will be consumed during operation. "Default" is 5V@500mA for USB2.0 and 5V@900mA for single lane of USB3.1.
After these processes, data channels and power supply are configured by using USB PD communication such Discovery and Configuration.
Roles defined on USB ports
Next, we will explain the roles defined on USB ports, including the legacy USB-A and USB-B connector. As shown in Table 1, USB ports have two roles defined: data and power.
Three data roles are defined: DFP and UFP, Dual Role Data (DRD), which allows switching between DFP and UFP. DRD is equivalent to OTG (USB On The Go). Similarly, three power roles are defined: Source-Only, Sink-Only, and Dual Role Power (DRP) that can switch between Source and Sink.
The DRP switches between source mode (Pull Up resistor on the CC line) and sink mode (Pull Down resistor on the CC line) and automatically indicates to the opposite device the supported roles until connected. In this case, it is not initially determined whether the product will be the source or the sink. Hence, there are DRPs called Try.SRC and Try.SNK to prior the power role (Source or Sink) when connected. Source (Default) DRP becomes the source when connecting and after connection, it will be able to change role to Sink. Sink (Default) DRP has the same function as Source (Default) DRP.
| Category | Role name | Description |
|---|---|---|
| Data Role | DFP | A port has the role of USB-A connector |
| UFP | A port has the role of USB-B connector | |
| DRD | A port that can be used as either DFP/UFP | |
| Power Role | Source-Only | A port for power provider |
| Sink-Only | A port for power consumer | |
| DRP | A port that can be used as either Source/Sink. Toggling (Source/Sink) | |
| Try.SRC (DRP) | DRPs that try to become Source-DFP as much as possible when connecting | |
| Try.SNK (DRP) | DRPs that try to become Sink-UFP as much as possible when connecting | |
| Source (Default) | Becomes a source without toggling when connecting, but Power Role Swap is possible | |
| Sink (Default) | Becomes a sink without toggling when connecting, but Power Role Swap is possible |
Since USB achieves data communication and power delivery on a single connector, it is necessary to define the role of the USB connector in terms of both data and power. As shown in Table 2, the combination of data role and power role is defined as a mandatory requirement that the source be DFP and the sink be UFP to maintain compatibility with USB-A and USB-B connectors. The USB data communication is defined as an option because a USB AC adapter does not necessarily require data communication.
| Roles on USB Type-C port | Data Role setting | UFP Function | DFP Function | ||
|---|---|---|---|---|---|
| DFP | UFP | USB Device | USB Host | ||
| Power Role setting | Source | Mandatory | Option | Option | Option |
| Sink | Option | Mandatory | Option | Option | |
| DRP | Mandatory | Mandatory | Option | Option | |
What kind of USB products and what roles do they play?
Next, let's take a look at what kind of product each role combination is used in.
The source/DFP role is the role for USB-A connectors in a PC and it provides power. So, a typical USB Type-C device with source/DFP role is an AC adapter. On the other hand, the sink/UFP role is the role for USB-B connectors in a peripheral device and it consumes power from USB. USB Type-C devices with sink/UFP role are peripheral devices such as headsets that consume the power from USB to operate. Many USB Type-C devices such as PCs and smartphones will have DRP/DRD roles. We can see that smartphones, PC docking stations, and USB hubs use the Try.SNK(DRP)/DRD role, and laptops, power banks, and even desktop PCs use the Try.SRC(DRD)/DRD role.
The case where a laptop PC connects to a docking station and the power supply is reversed from the docking station to the PC while maintaining the direction of data communication from the PC to the docking station, it is defined as Option in Table 2. In this case, the docking station becomes the source UFP referred to as the sourcing device and the laptop becomes the sink DFP referred to as sinking host. Combinations of these roles cannot be achieved by using only the normal connection sequence, but are achieved using Role Swaps, which will be described later.
The following section describes what role will determine when a DRP device is connected. As shown in Figure 9, when the power bank is connected to the AC adapter, because the AC adapter has source/DFP role, the Try.SRC(DRP)/DRD power bank cannot become the source, but is determined to be the sink/UFP role. Also, when the same power bank connects to a Try.SNK(DRP) /DRD smartphone, the power bank will become the source/DFP and the smartphone will become the sink/UFP.
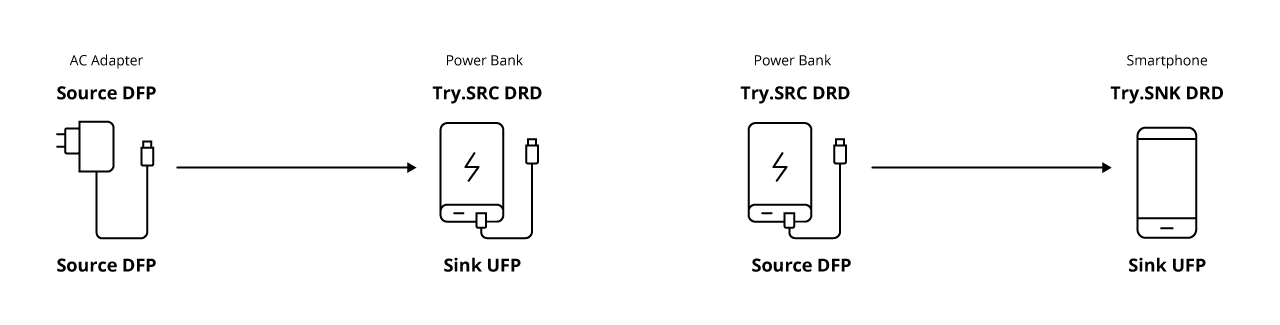
Figure 9: Example of role status for each device after connection
About Role Swap
The last section in this explanation is “Role Swap”. "Role Swap" means exchanging the roles of the USB ports. There are three categories of signaling on USB Type-C that have a role: data line, VBUS/GND line, and power supply VCONN for e-Marker on the cable. It is possible to exchange these three roles of the opposite device and itself. The specifications define in addition to fast role swap (FRS) as mentioned before, these three role swaps: Data Role Swap, Power Role Swap, and VCONN Role Swap.
USB ports are role-defined in terms of both data role and power role. Data Role Swap exchanges only their own data role (DFP or UFP) with its opposite device (UFP to DFP). Data Role Swap does not change the state of both VBUS/GND lines and VCONN line. Similarly, Power Role Swap allows to exchange only their own Power Role (Source or Sink) with its opposite device (Sink or Source). Again, Power Role Swap ensures that the state of both data lines and VCONN line are not changed.
When connecting DRD/DRP devices to each other, it is not initially determined whether products will be the source or the sink. Therefore, when a laptop PC connects to a docking station as shown in Figure 10, the power supply from PC is reversed to PC from the docking station by using either Data Role Swap or Power Role Swap while maintaining the direction of data communication from the PC.

Figure 10: Power Role Swap and Data Role Swap
VCONN Role Swap is for switching the device feeding power to the cable. Only devices that provide VCONN to cable are allowed to communicate with e-Marker. For example, when communicating in alternate mode or USB4, when the DFP port does not supply VCONN to cable and the DFP port needs to communicate with the e-Marker, DFP port should supply VCONN to cable by using VCONN Role Swap before accessing to the e-Marker.
Role Swap is performed by USB PD communication.
In our next session, we will look at safety technologies in USB PD.
Module List
- USB Power Delivery (1) Enhanced Convenience in USB Charging
- USB Power Delivery (2) The Technology 1 - Convenience and Safety
- USB Power Delivery (3) The Technology 2 - USB Type-C and Role Swap
- USB Power Delivery (4) USB PD Safety Implementation
- USB Power Delivery (5) Faster Development with Renesas Solutions