The Security Renesas Solution Starter Kit (RL78/F24 Security RSSK) for RL78/F23, F24 introduced in Part 2 of the September 2022 Blog “First Security Solution for the 16-bit RL78 Automotive MCU Makes Its Debut!” has been completed. It will be officially released in 1Q of 2024.
RL78/F24 Security RSSK can perform security functions such as encryption/decryption, secure boot, key registration, random number generation, and challenge and response (C&R) using only the built-in software (Hello world) and GUI tool operations. Users with a signed NDA can use it to develop security functions, and users without NDA unsigned can use it to study security. In addition to the security dedicated board, a USB cable and CD-ROM (containing GUI tools, manuals, etc.) are included in the package. Users can get started right away once installing the GUI tools onto your computer and connecting the board to the computer with the USB cable.
Figure 1 shows the RL78/F24 Security RSSK board layout. It is equipped with Debugger I/F (E2/E2-lite connection), Communication I/F (CAN/CAN FD I/F, LIN I/F) and USB (Micro B) - serial I/F (serial communication, power supply). The initial setting is debugger connection disabled. By passing NDA authentication, you can connect to a debugger and write and debug user programs. C&R is used for NDA authentication (see Figure 2). EEPROM is used for reprogramming demonstration.
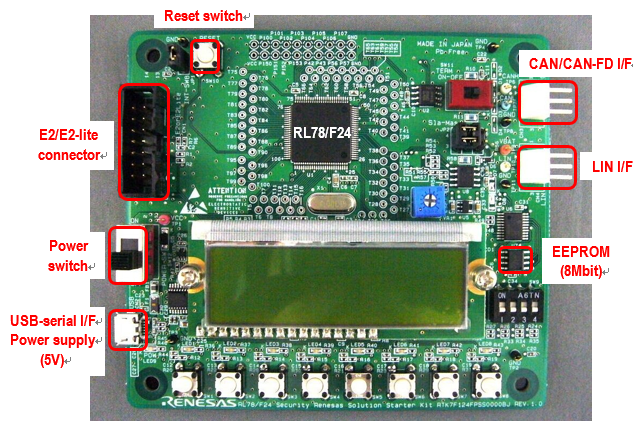
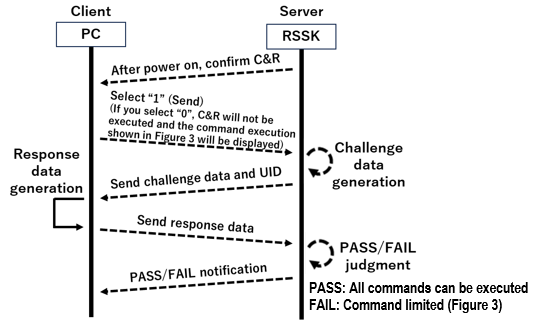
Table 1 shows the main functional differences between NDA signed/unsigned. In addition, if NDA unsigned users conclude NDA after purchasing RL78/F24 Security RSSK, there is no need to repurchase RL78/F24 Security RSSK again. By passing NDA authentication, Functional restrictions can be removed.
| Function | NDA signed users | NDA unsigned users |
|---|---|---|
| Hardware Board | Security dedicated board with RL78/F24 written with sample key and software (Hello world) | Security dedicated board with RL78/F24 written with sample key and software (Hello world) |
| Software GUI tool (CD-ROM included) |
|
|
| SETUP procedure | NDA authentication with C&R, debugger connection can be enabled with authentication PASS | Only connect PC and USB *Debugger cannot be connected |
| Encryption/Decryption | Possible | Possible |
| Key registration | Possible | Impossible *Only registered keys for samples can be used. |
| CMAC creation/verification | Possible | Possible |
| Secure Boot by HW | Possible | Impossible |
| Secure Boot by SW | Possible | Possible *Only PASS/FAIL can be confirmed |
| Random number generation | Possible | Possible |
| Initialize key storage | Possible | Impossible |
| C&R experience | Possible | Possible |
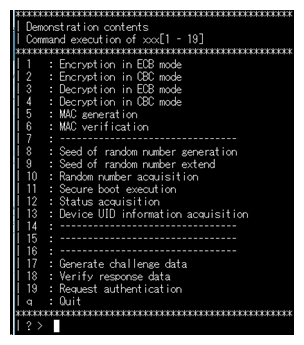
Figure 3 shows the command execution launched by NDA unsigned users through serial communication using a terminal emulator (Tera Team is used in the figure). It is possible to select the displayed items 1 to 19 to execute security functions. By passing NDA authentication, all items will be displayed for NDA-signed users.
Following are GUI tools included on the CD-ROM.
BOOT_LOADER_SETTING_TOOL
This tool can only be used by NDA-signed users. It is possible to generate MAC for Secure Boot (hardware) and create rfp-cli communication commands for RFP (Renesas Flash Programmer). The created communication command can be written to Code Flash of RL78/F24 via the debugger.Image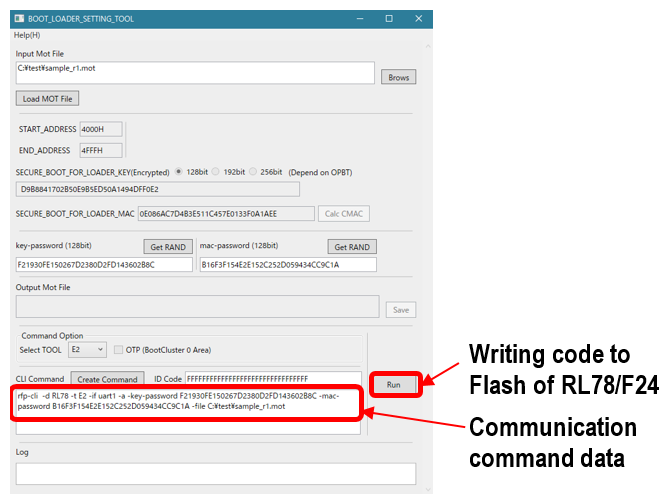
Figure 5 BOOT_LOADER_SETTING_TOOL KEY_SETTING_TOOL
This tool can only be used by NDA-signed users. It consists of 4 tabs: [M1-M5 [SHE standard]], [M1-M5 [SHE extended]], [Key storage information] and [Get ID]. At startup, only [Get ID] is active, NDA authentication is performed when GET ID is executed, and all tabs are active if the user has signed the NDA.
Figure 6 shows [M1-M5 [SHE standard]]. When you fill in the necessary items, select them, and execute, SHE standard M1 to M5 data and the key used for data generation will be displayed. There is no need to perform complex and difficult calculations.Image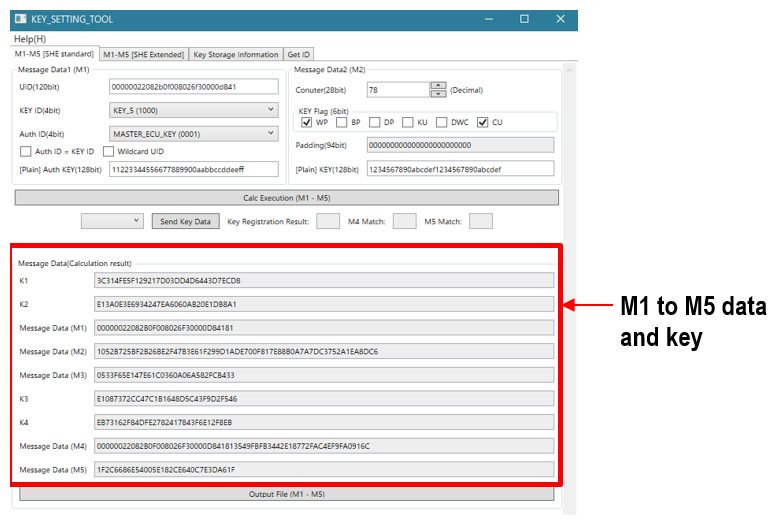
Figure 6 KEY_SETTING_TOOL (128bit key registration data generation)
Figure 7 shows the key information stored in Key storage. KEY_ID/KEY_NAME, key length, counter, key flag, key validity, and Key storage active block (A or B) are displayed.Image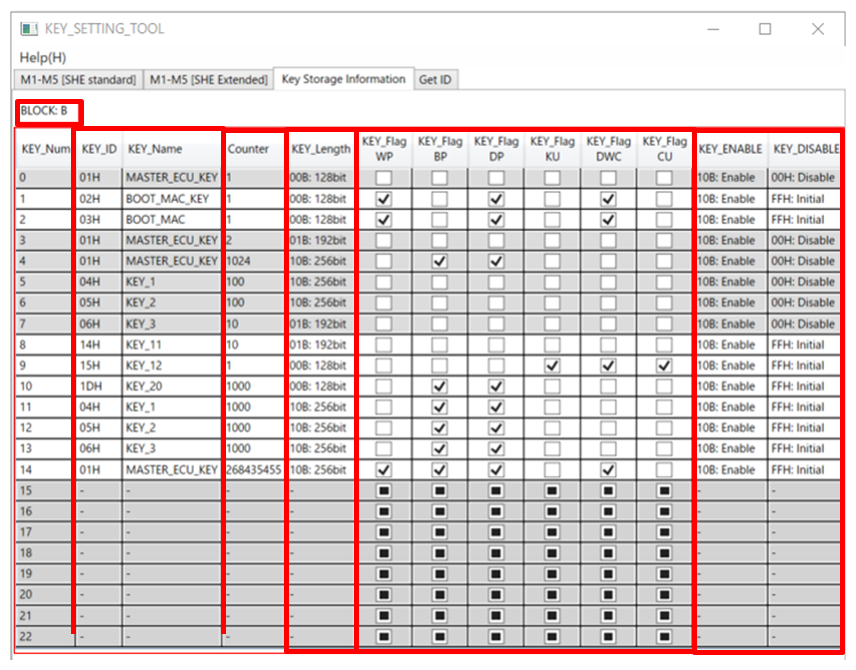
Figure 7 KEY_SETTING_TOOL (key storage information) C&R_TOOL
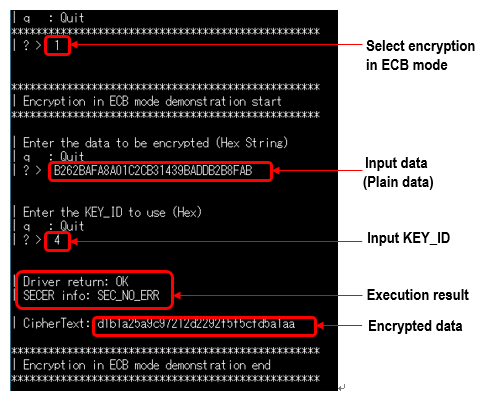
It is possible to generate challenge data, response data, and verify response data. Figure 8 shows the response data generation. Select Response Generation, enter the necessary items, and then execute (RUN) to display the response data in the RESPONSE column. There is no need to perform complex and difficult operations such as KDF (key derivation function) or CMAC operations.
Image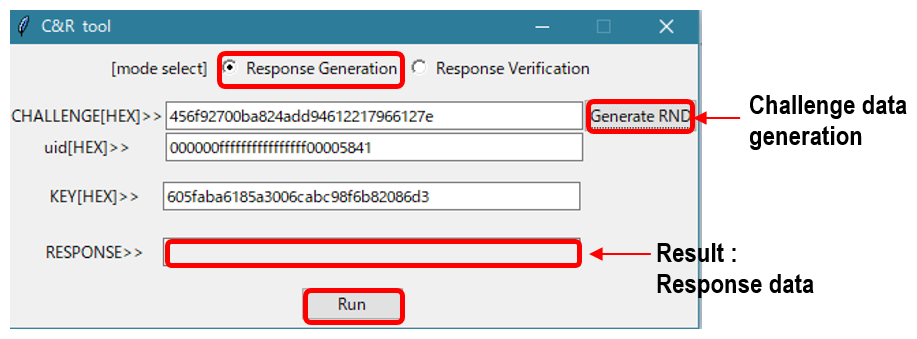
Figure 8 C&R_TOOL (Response data generation)
Figure 9 shows the response data verification. Select Response Verification, enter the necessary items, and then execute (RUN) to display the results in a pop-up.
Image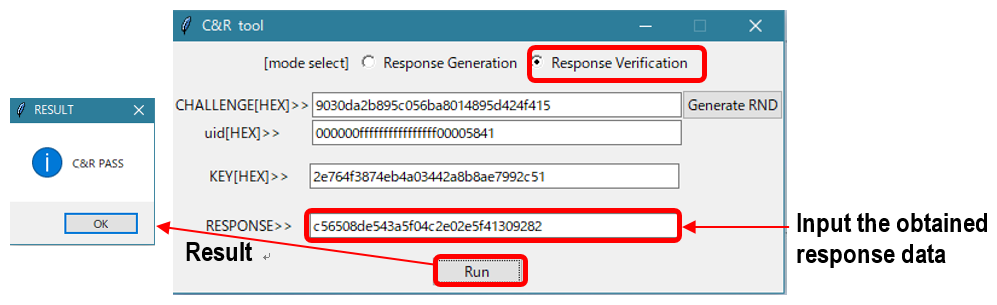
Figure 9 C&R_TOOL (Response data verification)
Solutions provided by this RSSK can be adapted to a variety of needs, such as those who want to efficiently develop security software in a short period of time without spending man-hours, those who want to automate difficult calculations, those who simply want to use security functions, and those who want to study security functions. Please take advantage of it.
Finally, Table 2 shows the security software provided free of charge. Although there is no guarantee or support, the source code is provided.
| Item | Description | Release | |
|---|---|---|---|
| Official version | Site | ||
| AESEA Sample Security Driver* | Software for encryption/decryption, secure boot, CMAC generation, and verification based on AES encryption algorithm | Available (ver.1.21) | Security dedicated website (Secure Portal) |
| SHA-256/384/512 | Software library for calculating hash values Output 256/384/512bit message digest | Available (ver.1.00) | Secure Portal Products web page |
| RSA-2048/3072 | Software library for signature generation and verification of RSASSA-PKCS1-V1.5 with key length of 2048/3072 bit | Available (ver.1.01) | Secure Portal Products web page |
| ECDSA* | Software library for signature verification using elliptic curve digital signature algorithm | Dec-23 | Secure Portal |
* NDA signed users only
If you are interested, please contact your local distributor or Renesas sales representative.
